Cyber ThreatHunt Operation

Cyber ThreatHunt Operation is a process of pro-actively searching through networks and endpoints to detect and isolate advanced threats. Analyze any suspicious behavior or activity or to uncover hacking attempt and malicious actors who have bypassed traditional re-active security solutions.
Cyber ThreatHunt Operation will focus on identifying suspicious activities, indicators of compromise (IoCs), malware infections, unknown threats and new adversary TTPs (Tactics, Techniques and Procedures) that may compromise the organizations internal networks or systems.
Cyber ThreatHunt Operation Benefits
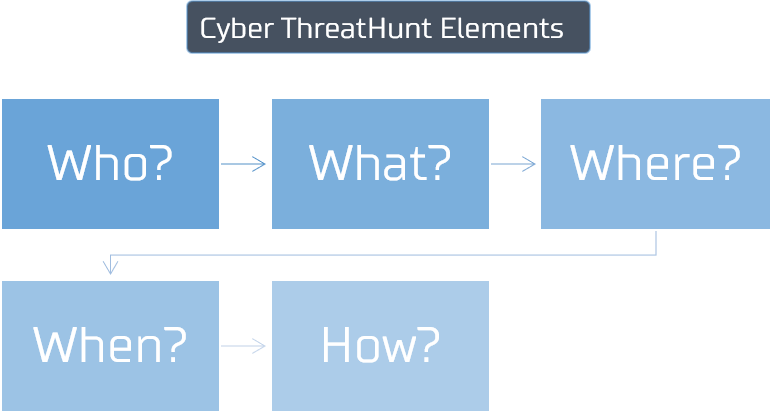
Are you hacked
Cyber Hunt Operation searches the network of the organization looking for any Indicators of Compromise (IoC) uncovering targeted attacks, when it happened and who’s behind it.
How were you hacked
Cyber Hunt also aims to identify the vulnerabilities through which the hackers penetrated the network of the organization.
Penetration depth
Cyber Hunt aims to detect the extent to which the attackers have reached inside the network.
Destroy Cyber Kill Chain
After detection of any compromise, Cyberkov will shutdown the communication between the attacker and the compromised machines to contain the threat and minimize any potential damage.
Cyber TheatHunt Operation Methodology
>SaturoS_ follows industry standard best practices and methodology when hunting for cyber threats.
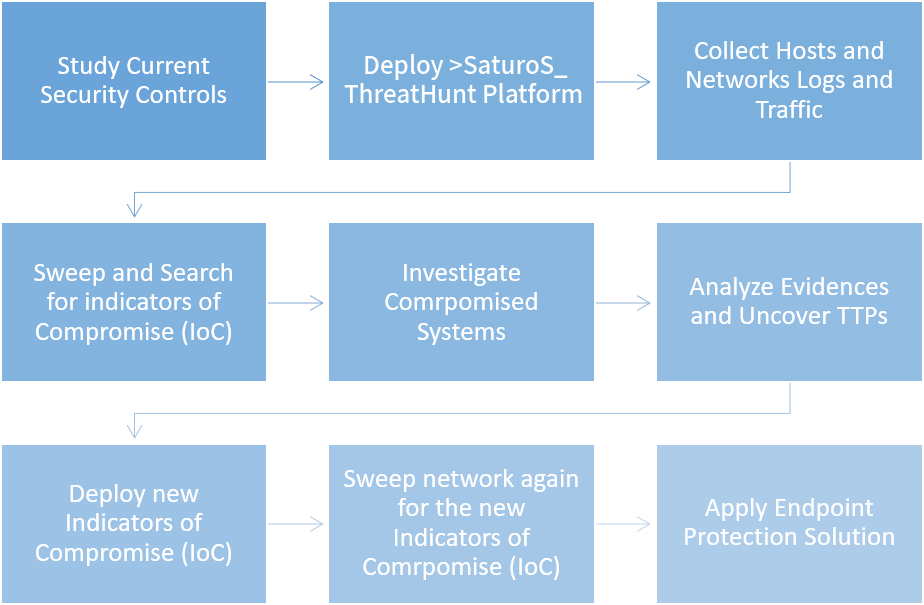
- 1- Study Current Security Controls
- 2- Deploy Cyberkov ThreatHunt Platform
- 3- Collect Hosts/Networks Logs and Traffic
- 4- Sweep and Search for indicators of Compromise (IoC)
- 5- Investigate Compromised Systems
- 6- Analyze Evidences and Uncover TTPs
- 7- Deploy new Indicators of Compromise (IoC)
- 8- Sweep network again for the new Indicators of Compromise (IoC)
- 9- Apply Endpoint Protection Solutions
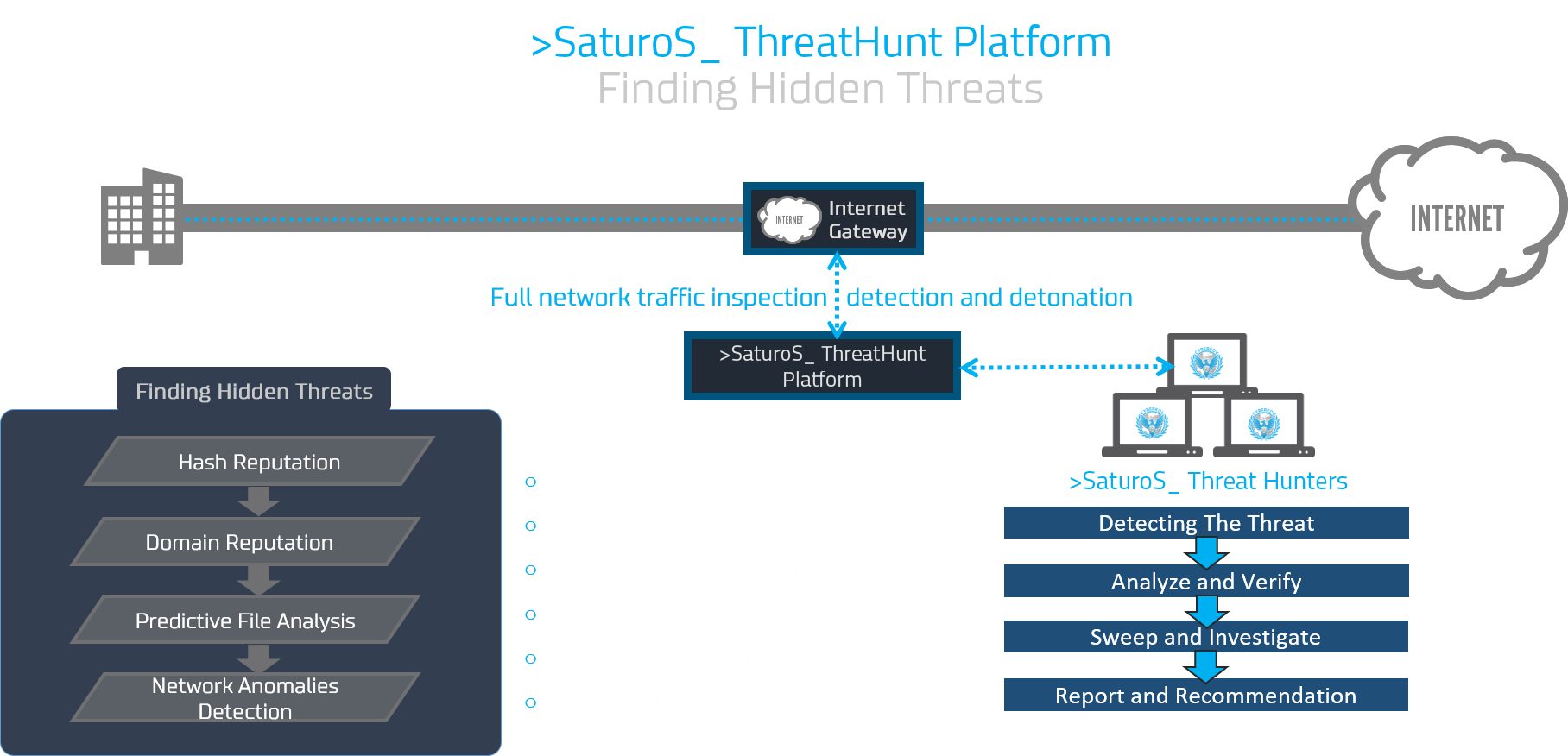
>SaturoS_ ThreatHunt Platform
The Cyber ThreatHunt Operation start with deploying >SaturoS_ ThreatHunt Platform which consist of multiple comprehensive security solutions to cover the internal network by analyzing the entire network traffic looking for adversaries hiding inside the networks and advanced malwares used in targeted cyber-attacks.
Cyber ThreatHunt Process

Automatic Process
In which a security analyst utilizes a software that leverages machine learning and user and entity behavior analytics (UEBA) to detect the potential risks. The analyst then investigates these potential risks, tracking suspicious behavior in the network

Manual Process
In which a security analyst searches through various data sources using their own knowledge and techniques and familiarity with the network to create hypothesis about potential threats, such as Lateral Movement by Threat Actors